As much as we might wish we lived on an ethereal plane with our beloved gadgets, we don’t (yet), and their physicality can be a burden. While annoying design flaws like the iPhone 4’s antenna problems regularly hammer this point home to us, there are potentially graver security implications. A recent study conducted by the University of Pennsylvania’s Department of Computer and Information Science points out one major flaw that should give touchscreen smartphone users some pause: The smudges our fingers leave on the screens can be used to guess our passwords. By taking photos of several Android smartphones and upping the contrast, researchers were able to figure out the phones’ password 92% of the time.
“Touchscreens are touched, so oily residues, or smudges, remain on the screen as a side effect,” the report said. “Latent smudges may be usable to infer recently and frequently touched areas of the screen – a form of information leakage.”
The researchers tested Android handsets because the Google OS uses a graphical password, with users tracing a pattern on the phone to unlock the device. In ideal lighting conditions, the researchers managed to decipher the phone’s password 92% of the time by taking photos of the screen and bumping up the contrast.
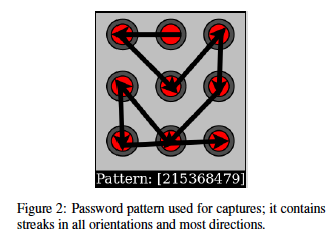
There are a few grounds on which to pick apart the study. 92% sounds like an awfully high percentage, and it may indeed be overinflated: While they note that “the pattern space contains 389,112 distinct patterns,” the researchers used the same password for all of the tests, 215368479. They did this because it contained streaks in every orientation and most directions; however, it’s possible that if they were forced to truly guess random passwords from real-world users’ phones, they might have encountered different results.
More broadly, Android phones present a particularly ripe target for smudge attacks due to the pattern-based unlock mechanism; 389,112 may sound like a large number of possibilities, but from a cryptographic perspective it really isn’t; an iPhone, with its more conventional password system of letters and numbers entered in sequence, would probably be a tougher nut to crack by smudge attack.
Still, the results are sobering, and the researchers point out that they could potentially apply to many touchscreen devices beyond smartphones, including touchscreen ATMs and DRE [direct-recording electronic] voting machines. As “smudges are surprisingly persistent in time [and] it is surprisingly difficult to incidentally obscure or delete smudges through wiping or pocketing the device,” the research team provides one bit of advice that’s good even if you’re not worried about smudge attackers: Clean your devices regularly.
You can read the full PDF of their research paper here.
(PC Pro via Slashdot. title image via Android Community)








